ArcSight ESM Interview Questions
Last updated on Jan 22, 2025
Arcsight ESM is in much demand among the companies due to various benefits that it provides. The companies have started to adopt ArcSight in order to minimize their digital security related risks. This adoption has led to mass scale recruitment in the companies for an ArcSight Resource.
Here is an ArcSight Interview Guide that contains Arcsight Interview questions. These interview questions are divided into two categories- Arcsight interview Questions for Fresher and Arcsight interview Questions for Experienced professionals.
Most Frequently Asked ArcSight ESM Interview Questions
Interview Questions for fresher:
The fresher interview is unlike any other job interview: it’s a specialized, rigorous process that tests your basics, problem-solving abilities, and personality. So, go through the basics first. This document will help you achieve it.
What is the ArcSight tool?
Ans: ArcSight ESM is a market-driving answer for gathering, associating, and providing details regarding security occasion data. Utilizing a large number of various kinds of gadgets and application connectors, ArcSight ESM gives the main issue to the investigation of everyday business tasks.
What does ArcSight ESM stand for, and what is its primary use?
Ans: ArcSight ESM represents Enterprise Security Manager.
As the name itself infers, the utilization of this instrument is that it increases the value of your association security approaches. Utilizing this device will assist the associations with focusing on the danger identification, investigation on the triages, consistency of the executives. These are done on the SIEM stage, where it lessens the time taken to determine a cybersecurity danger.
Want to Become a Master in ArcSight? Then visit here to Learn ArcSight Online Training
How does it work?
Ans: ArcSight adopts a comprehensive strategy to security insight, interestingly binding together Big Data assortment, organize, client and endpoint monitoring what's more, legal sciences, and propelled security examination. Powerful out-of-the-case use cases incorporate continuous danger identification and reaction, consistent robotization and confirmation, and IT operational insight. Depend on the security aptitude, experience and authority of the ArcSight group for your SIEM needs. ArcSight has been recognized as Enchantment Quadrant Leader by Gartner for the past 12 years, longer than any current seller—a demonstration of the force and adequacy of the arrangement.
What does ArcSight ESM help you with?
Ans:
- Relate information from any source continuously to recognize occurrences before they become penetrate.
- Resolve gives quicker: Answer who did what? Where? When? Also, how?
- Gather, store, and examine any occasion from any source and whenever.
- Discretionary consistence packs empowered bundled reports for PCI, SOX, and IT Governance
- Assemble and keep up security activity focus (SOC) through enormous information security investigation.
- Incorporate SOC across IT with arranging activities, administration work area, CMDB, business insight, Hadoop, email security, application security, danger takes care of, and so forth.
- Unrivaled broadness, profundity, and speed of occasion assortment with licensed log the executives' apparatuses
ArcSight ESM gives an essential issue to the examination of the day by day business tasks. Equipped with this information, the ongoing relationship capacities of ArcSight ESM can recognize surprising or unapproved exercises as they happen. At last, the perception and revealing abilities of ArcSight ESM bolster customized dashboards and on-request or planned reports for directors, supervisors, or examiners.
What does SIEM stand for, and what is it about?
Ans: SIEM represents Security Information and Event Management.
So this is where an all-encompassing perspective on the security procedure executed inside the association. The letter e is quiet, and it is tended to as the "SIM" stage. Mostly, in this procedure, the information is assembled into one secure store where the logs are utilized for future security examination. This procedure is generally used in the Payment Card Industry. It is delegated an information security standard in the Payment Card Industry.
How does SIEM ArcSight work?
Ans:
Security data and occasion the executives (SIEM) programming gives undertaking security experts both knowledge into and a reputation of the exercises inside their IT condition. SIEM innovation has been in presence for over 10 years, at first developing from the log the board discipline.
It joined security occasion the board (SEM) – which examines log and occasion information continuously to give danger observing, occasion connection and episode reaction – with security data the executives (SIM) which gathers, investigates and gives an account of log information.
SIEM works by joining two advancements: a) Security data the board (SIM), which gathers information from log records for examination and reports on security dangers and occasions, and
b) security occasion the executives (SEM), which leads continuous framework observing, advises arrange administrators about significant issues and builds up connections between security occasions.
What does SIEM tool provide:
- Continuous deceivability over an association's data security frameworks.
- Occasion log the board that solidifies information from various sources.
- A connection of occasions assembled from various logs or security sources, utilizing on the off chance that decides that add knowledge to crude information.
- Programmed security occasion notices. Most SIEM frameworks give dashboards to security issues and different strategies for direct warning.
What are the advantages of SIEM software?
Ans:
- Across the board SIEM machine for general log the board, consistence, and occasion the board
- Collect, store, and break down your security occasions through a solitary machine
- Analyze billions of security occasions from firewall, IPS, endpoint, applications, and streams
- Built-in discretionary review reports to aid consistence
- Detect dubious and malignant conduct missed by your point security gadgets
- Combat APTs, malware assaults, and insider dangers
- Protection against zero-day dangers
How does ESM and SIEM relate?
Ans: ESM incorporates danger insight, takes care of, connection, investigation, profiling, security alarms, information introduction and consistence. It offers knowledge and joining to organize, examine and react to dangers, while the installed consistence structure and implicit security content packs improve examiner and consistence tasks.
ESM is the center result of SIEM arrangement portfolio, which incorporates Enterprise Log Manager (ELM), Advanced Correlation Engine (ACE), Event Receiver (ERC), Database Event Monitor (DEM), Application Data Monitor (ADM) and Global Threat Intelligence (GTI). ESM offers incorporation with many integral occurrences of executives and investigation arrangements, including Threat Intelligence Exchange. In view of endpoint observing, it totals low-commonness assaults, utilizing worldwide, outsider, and nearby danger knowledge.
What is ArcSight Express?
Ans: ArcSight ESM Express, the across the board SIEM machine, is a ground-breaking danger discovery, reaction and consistent board stage. It consolidates the best of the board and security occasion the board to push you to drastically chop down an opportunity to identify and react to dangers.
) What all components it has, and what is their role?
Ans: ESM - The ArcSight Manager is the core of the arrangement. It is a Java-based server that drives examinations, work processes, and administrations. It additionally associates yield from a wide assortment of security frameworks.
Keen Connector - SmartConnectors assemble and process occasion information from end gadgets and pass it to the Manager.
ArcSight Console - The ArcSight Console is a workstation-based interface expected for experts and administrators. It is the composing apparatus for building filters, rules, reports, Pattern Discovery, dashboards, and information screens. It is likewise the interface for overseeing clients and the work process.

Arcsight Training
- Master Your Craft
- Lifetime LMS & Faculty Access
- 24/7 online expert support
- Real-world & Project Based Learning
) What are the connectors?
Ans: SmartConnectors facilitated separately, or as a feature of an ArcSight Connector Appliance, are the interface to the items on your system that produce important relationship information on your system. After gathering occasion information from organizing hubs, they standardize the data in two different ways: normalizing values, (for example, seriousness, need, and time region) into a typical configuration, and normalizing the information structure into a standard construction.
Interview Questions for experienced:
The experienced interview is unlike any other job interview: it’s a specialized, rigorous process that tests your basics along with skills, problem-solving abilities, personality and deep core knowledge of the domain and its working. So, go through the basics first. This document will help you achieve it.
Related Article: HP Arcsight ESM Security Administrator Training
) What are the four pillars of ESM?
Ans:
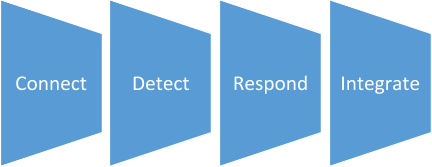
) Explain the four pillars of ESM?
Ans: Connect
ArcSight ESM use the Security Open Data Platform, whose Smart Connectors can associate with 450+ information source types to gather, total, clean, and enhance your information before taking care of it into your security investigation. By organizing your information, ESM makes it both increasingly valuable and more practical. It's additionally adaptable, so you don't need to stress over information development.
Detect
Ongoing connection offers the quickest method to distinguish and raise known dangers – and ArcSight shows improvement over anybody. Upheld by knowledge takes care of, disseminated relationship, adaptable rulesets, layered examination, network content, and the Activate structure, ArcSight is prepared to scalably address any SIEM use case your association faces, regardless of how mind boggling.
Respond
Empower your SOC with quick, productive danger reaction. ArcSight empowers both straightforward and complex mechanized reactions, out-of-the-crate, that can be activated on-request or by explicit alarms. It can even report back if extra reaction is required. Moreover, ArcSight additionally coordinates with driving SOAR and computerized work process arrangements, for example, ATAR Labs and ServiceNow.
Integrate
ArcSight's open design empowers it to trade information, bits of knowledge, and cautions with your current security examination arrangements, including ArcSight Interset, ArcSight Investigate, and our numerous ArcSight accomplices. This layered investigation approach enables ESM to convey considerably increasingly successful danger identification with less bogus positives and progressively enlightening cautions, for a progressively productive SOC.
) How does the ArcSight architecture work?
Ans: Individual Smart Connectors, as well as a Connector Appliance, accumulate and process occasion information from organizing gadgets and pass it to the Manager. The Manager procedures and stores occasion information in the CORR-Engine. Clients screen occasions in ArcSight Web and oversee client gatherings and the CORR-Engine stockpiling utilizing the ArcSight Command Center, and create content and perform propelled examination on the ArcSight Console. A far-reaching arrangement of discretionary items give measurable quality log the board, organize the executives and moment remediation, administrative consistence, and propelled occasion examination.
) How can the security information and event management process of SIEM can be broken down?
Ans:
- Information assortment – All wellsprings of system security data, e.g., servers, working frameworks, firewalls, antivirus programming and interruption counteraction frameworks are designed to take care of occasion information into a SIEM tool.Most current SIEM instruments use operators to gather occasion logs from big business frameworks, which are then handled, sifted and sent them to the SIEM. Some SIEMs permit agentless information assortment. For instance, Splunk offers agentless information assortment in Windows utilizing WMI.
- Approaches – A profile is made by the SIEM director, which characterizes the conduct of big business frameworks, both under ordinary conditions and during pre-characterized security occurrences. SIEMs give default rules, cautions, reports, and dashboards that can be tuned and modified to fit explicit security needs.
- Information solidification and relationship – SIEM arrangements combine, parse and investigate log documents. Occasions are then classified dependent on the crude information and apply connection decides that consolidate singular information occasions into significant security issues.
- Notification – If an occasion or set of occasions triggers a SIEM rule, the framework advises security staff.
) Explain how ArcSight ESM is protecting businesses across the globe?
Ans: Coming up next are the various ways that the business is ensured by utilizing the ArcSight ESM device, as follows:
- It is equipped for gathering information or data from a log source
- It immensely diminishes the reaction time and helps in decreasing the harm also
- It can proficiently store data where the data can be recovered as we, for the most part, do in big business level databases.
- It gives pertinent job reports that are accessible inside the undertaking
- The engineering is adaptable and is effectively adjustable and keeps up the superior framework
) How does ArcSight ESM provide a Powerful real-time data correlation?
Ans: Indeed, ArcSight ESM gives incredible continuous information connection by handling the number of occasions every second. Because of this investigation, an increasingly exact result is proposed. So dependent on this investigation, the dangers that disregard the inward standards are heightened inside the stage. ESM really forms 75,000 occasions for every subsequent premise.
) Why do organizations need Security Information and Event Management systems?
Ans: A large portion of the little organizations needs more labor to ensure that their security procedure is unblemished. Yet, they won't have the option to be proactive and caution the group that there may be a potential danger assault; this is because they don't have any programmed component which triggers a dangerous assault. So to explain the constant issue and ensure the security checks are observed and broke down, we have a Security Information and Event Management framework. Out of this framework is ArcSight SEM. So mostly, all the machine log information is dissected and comprehends the examples of exemplary conduct versus irregular conduct. Along these lines making it an ideal apparatus where it can understand the security logs up until now and dependent on the investigation can trigger some data which may forestall a greater danger to the whole association.
) Explain how a SIEM can meet the PCI DSSrequirements?
Ans:
Unapproved arrange association recognition – PCI DSS consistent associations need a framework that distinguishes all unapproved arrange associations with/from an association's IT resources. A SIEM arrangement can be utilized as such a framework.
Looking for uncertain conventions – A SIEM can report and legitimize the utilization of an association's allowed administrations, conventions and ports, just as record security highlights actualized for unreliable conventions.
Investigate traffic streams across DMZ – PCI consistent associations need to actualize a DMZ that oversees associations between untrusted systems (e.g., the web) and a web server. Also, inbound web traffic to IPs inside the DMZ should be constrained while active traffic managing cardholder subtleties must be assessed.
SIEM arrangements can meet these necessities by assessing traffic that streams over the DMZ to and from interior frameworks, and by writing about security issues.
) What does ArcSight Logger do?
Ans: Along these lines, ArcSight Logger is only a log the board arrangement that can be utilized generally in security rehearses. So using the mechanism, the clients will have the option to catch and examine distinctive sort of log information and give valuable contributions to all the person's groups, so their inquiries are replied. In the end, this can be ventured into an endeavor level log the executives' arrangement if necessary.
So utilizing this arrangement points like consistency and hazard, the executives are taken into due thought. Likewise, the information can be used for looking, ordering, detailing, examination purposes, and maintenance also.

Subscribe to our YouTube channel to get new updates..!
) Wow, Archsight is comparable to other SIEM tools out there in the market viz. RSA envision, McAfee electronic warfare, etc.?
Ans: All unique SIEMs doesn't have a different undeniable reassure for administrator and investigation reason. Conjointly unique SIEMs don't have Smart Connectors, which can do the resulting functionalities. Gather all the data you might want from a graceful gadget, along these lines, and you are not getting the opportunity to come back to the device all through the Associate in Nursing examination or review. Spare system data measure and space for putting away by sifting through the information you perceive won't be required for investigation. Dismantle singular occasions and standardize them into a standard composition (position) to be utilized by electronic fighting—blend opportunities to reduce the number of events sent to the Manager.
We have the perfect professional ArcSight Tutorial for you. Enroll now!
) Can you please share the Arcsight Dashboard and also the functions?
Ans: Dashboards show markers that convey the condition of your endeavor as reportable by Smart Connectors from information sources on your system. Dashboards territory unit made of individual information screens as well as question watchers in a surpassing style of graphical and understandable configurations that sum up the occasion stream and convey the effect of occasion traffic on explicit frameworks on the system or show the remainder of electronic fighting parts. The insurance Activity Statistics dashboard is one among the quality dashboards that display a spread of framework standing information screens, that convey the condition of your system security conjointly you'll have the option to deliver bespoken dashboards according to the earth.
) What is the Arcsight Corr engine?
Ans: The Correlation Optimized Retention and Retrieval (CORR) Engine is private information stockpiling and recovery structure that gets and forms occasions at high rates and performs fast pursuits. Events are put away in the CORR-Engines occasion maintenance period, where relationship activities happen, at that point, duplicated day by day into documents for long haul stockpiling. In all different SIEMs Corr motor is connection motor including ArcSight past versions(before 6.0)
) Few bullet points on ArcSight ESM?
Ans: Coming up next are the significant focuses on the ArcSight ESM instrument:
- With this instrument, heads and expert can distinguish more occurrences
- Operate all the more productively
- The same informational index can be utilized for the ongoing relationship of the information and log the executives' application can use the equivalent dataset.
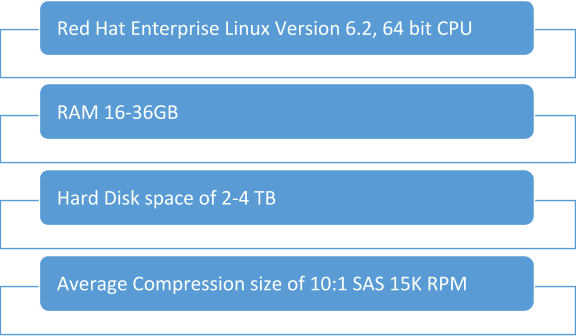
) What are the system requirements for implementing ArcSight ESM?
Ans: Supported Operating systems are:
) What does ArcSight Manager do, explain in brief?
Ans: The utilization of ArcSight chief is to just set up robust security boundaries inside the association. So it is one of the elite help motors which channels, oversees, associates all security-related occasions that are gathered by the IT framework.
The main parts that are essential for the ArcSight manager to work appropriately are:
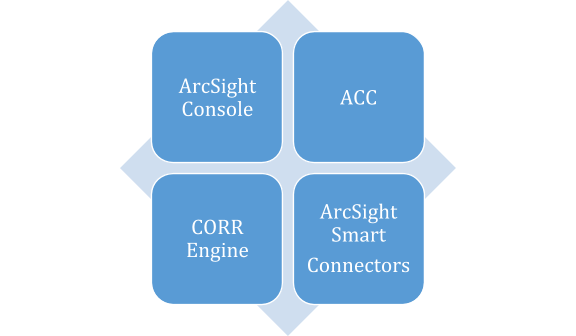
The operational environment for ArcSight Manager is nothing but the underlying OS and the file system that are in place.
) What does IDS stand for?
Ans: IDS stands for "Intrusion Detection System." This is the main component when it comes to ArcSight ESM. An Intrusion Detection System (IDS) is a framework that screens organize traffic for dubious movement and issues cautions when such action is found. It is a product application that checks a system or a framework for hurtful action or strategy penetrating. Any pernicious endeavour or infringement is ordinarily detailed either to a director or gathered midway utilizing a security data and occasion the board (SIEM) framework. A SIEM framework coordinates yields from numerous sources and uses caution sifting procedures to separate malevolent action from bogus alerts.
) Where is that the knowledge holds on primarily in ArcSight: electronic warfare or Logger?
Ans: If there's no feller in your atmosphere, electronic warfare can store all data. If you are a feller out there, you are saving knowledge. Thus, ArcSight feller is nothing anyway a log the board answer that might be utilized generally in security rehearsals. Along these lines exploitation answers, the clients are prepared to catch and break down a totally unique assortment of log information and flexibly fundamental contributions to all or any person's gatherings in this way their questions region unit replied. In the long run, this could be extended into an Associate in nursing venture level log the executives answer whenever required.
So exploiting this answer, subjects like consistency and hazard in the management region unit are taken into due idea. Likewise, the data will be utilized for looking, ordering, revealing, examination capacities, and maintenance moreover.
) What area unit devices will we monitor victimization ArcSight?
Ans: We can monitor any devices that all area units are generating logs. If ArcSight connectors support the logs, we will directly use suitable connectors. For different non-supported devices, we've to develop custom connectors.
ArcSight electronic fighting truly helps the associations and furthermore the individuals as underneath:
- All the occasion information is gathered midway and hang on and screen
- Easy to understand consistency reportage AN exceedingly in a solitary piece gives vital information in a satisfactory organization.
- It has the capacity to watch and relieve the opportunity.
- Wipes out manual technique the most extreme sum as achievable
- Spares important long stretches of security investigator any place they pay on bogus cautions
- Carries attention to the group concerning the assurance strategy in situ and furthermore the countermeasures upheld.
) What are the general observing boundaries for middleware applications like SharePoint?
Ans: Application logs, get to logs can be screen. In backend on the off chance that the application is utilizing a database, at that point database review logs can be screen
) What are the highlights of SIEM?
- Log the board
- Log observing
- Dashboard
- Design revelation
- Asset demonstrating and a lot more highlights
) Are we utilizing ArcSight? How might we secure our application condition?
Ans: Since ArcSight is a SIEM device where we can screen the logs for any vulnerabilities, so by utilizing this ArcSight, we can make aware of the application proprietor for dubious movement.
) What region unit the key choices of the ArcSight Enterprise Security Manager?
Ans: The key choices of the ArcSight Enterprise Security Manager Area unit as follows:
- Enhanced Security Event information
- Incredible period information visual picture and connection
- Machine-controlled work processes
- Security technique upgraded
- ArcSight Enterprise Security Manager device is perfect with ArcSight information Platform and ArcSight Investigate
) Present a defence for anyway ArcSight electronic fighting is defensive organizations over the globe?
Ans:
- The resulting territory unit the different manners by which the business is genuinely secured by exploitation ArcSight electronic fighting device, as follows:
- It's fit for assortment information or information from any assortment of log gracefully
- It hugely diminishes the inactive period and conjointly helps in lessening the mischief moreover
- It will quickly store information any place the information will be recovered as we tend to commonly kill undertaking level databases.
- It gives job applicable reports that zone unit out there at stretches the venture
- The plan is ascendable
- Basically adaptable and keeps up the prevalent framework
nclusion
Ans: ArcSight adopts a comprehensive strategy to security insight, interestingly binding together Big Data assortment, organize, client and endpoint monitoring what's more, legal sciences, and propelled security examination. Security data and occasion the executives (SIEM) programming gives undertaking security experts both knowledge into and a reputation of the exercises inside their IT condition. The utilization of ArcSight chief is to just set up robust security boundaries inside the association. So it is one of the elite help motors which channels, oversees, associates all security-related occasions that are gathered by the IT framework.
Upcoming Arcsight Training Online classes
| Batch starts on 7th Mar 2026 |
|
||
| Batch starts on 11th Mar 2026 |
|
||
| Batch starts on 15th Mar 2026 |
|


