ArcSight Tutorial
Last updated on Nov 07, 2023
What is ArcSight?
ArcSight is an ESM platform which stands for Enterprise Security Manager. It is a tool that is designed and implemented for managing the security policies within an organization. It is used in detecting, analysing, and resolving cyber security related threats within a short duration of time. The ESM platform includes the products for collecting the events, real time event management, log management, automatic response, and compliance management.
Wish to make a career in the world of Arcsight? Then Start with HKR'S Arcsight online training
Briefing about the ArcSight Components
ArcSight describes the components of the security model consisting of security monitoring features and functionalities. ArcSight resolves the problems of several requirements by collecting and storing the data for long term use cases.
- The features include storage, reporting, searching, monitoring the use cases and finding the correlation among the products.
- It collects the information of log events from applications, clouds, network environments, endpoints, systems, security products.
- ArcSight correlates the data and stores the information for compliance use cases.
- Generating the automated alerts for the investigation work that is carried out on the data.

Arcsight Training
- Master Your Craft
- Lifetime LMS & Faculty Access
- 24/7 online expert support
- Real-world & Project Based Learning
ArcSight Components Classification
- Arcsight SIEM Platform
The Arcsight SIEM Platform environment includes the security and visibility operations which leverage the monitoring platform infrastructure. The platform captures, normalizes and categorizes all the events and logs from network and security devices.
2. ArcSight ESM
The ArcSight ESM has the capability of collecting the broad log information combined with the powerful correlation engine which can detect the threats from multiple products and alerts the customers to take action on the vulnerabilities.
We have the perfect professional HP Arcsight ESM Security Administrator Training for you. Enroll now!
3. ArsSight Logger
The ArcSight Logger provides the log management and storage capabilities with automated compliance reporting. It can store upto 42TB of log data that can search for multiple events per second over structured and unstructured data. It supports automated reporting for SOX, PCI DSS, NERC and other regulations.
4. ArcSight Express
The ArcSight Express includes the technologies of real-time correlation and log management from ESM and logger. The Express is referred to as “security expert in a box” which has several built-in correlation rules, dashboards and reports. It provides the deployment and low-cost monitoring solutions for the infrastructure.
5. ArcSight SmartConnectors
The ArcSight SmartConnectors collect the event data from network devices and normalizes the data structure into schema. The connectors can filter the data, save the network bandwidth and storage space. The SmartConnectors improves the efficiency by aggregating the events to reduce the quantity of the same type. The events can be categorized into readable format which makes it easier for using the events to build the filters, rules and reports.

Subscribe to our YouTube channel to get new updates..!
ArcSight ESM Network model
The ArcSight ESM Network model is the combination of network and assert models together builds the correlation criteria.
- The network model represents the nodes and characteristics of the network.
- The assert model represents the attributes of asserts.
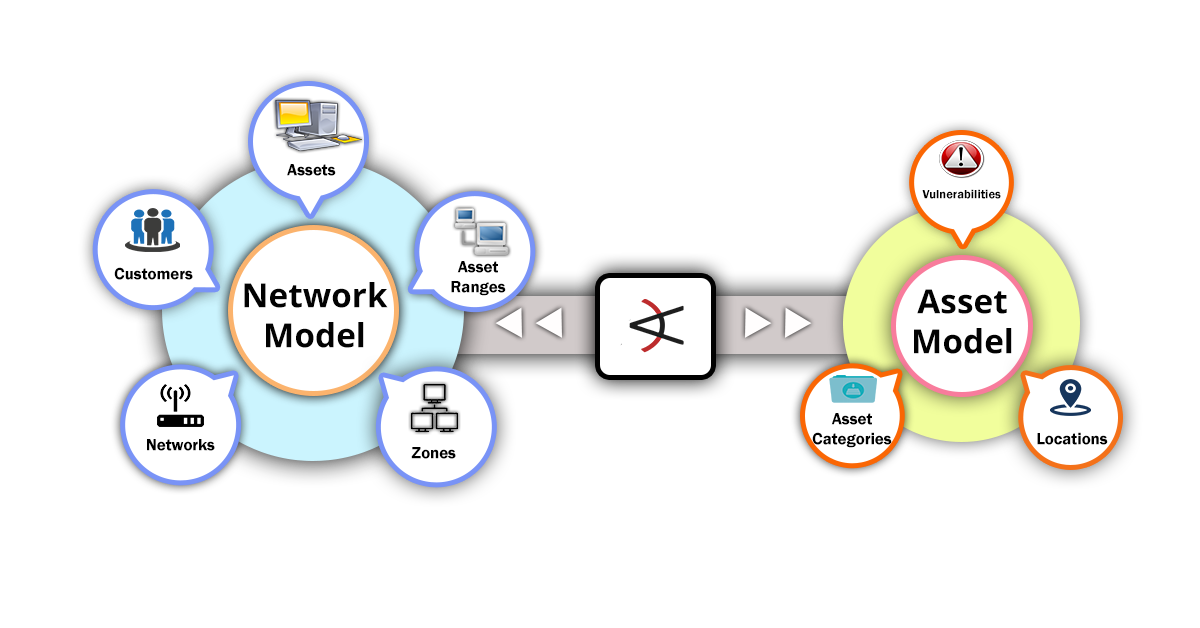
The elements of network model consists the following resources.
- Asserts - It represents the nodes on the network consisting the servers, routers and devices.
- Assert Ranges - It represents the set of network nodes with block of IP address.
- Zones - It represents the portion of network categorized by block of addresses.
- Networks - It differentiates the two private address spaces.
- Customers - These are the business units associated with the networks.
Asserts
- The Asserts resources identifies any network endpoint within an IP address, MAC address, host name, external ID.
- An assert resource is the specification of network identity which includes
Assert name.
Network IP address.
MAC address.
Host name.
External ID.
frequently asked Arcsight interview questions & answers
Assert Ranges
- An Assert Ranges is the group of asserts attached to a network that uses a block of IP address.
- When an event is processed by the SmartConnector, its endpoints are identified as a single asset or an asset that belongs to a particular assert range. A reference to an assert or assert range identifier is populated in the event schema.
Zones
- Zones usually represent a functional group within a network or a subnet such as LAN, VPN or DMZ identified with the block of IP address.
- Every assert or address range is associated with a zone. ESM is already configured with the global IP address which helps in resolving without setting up any additional zones.
- The address range in the zones in the same network cannot overlap.
- When SmartConnector processes an event, it evaluates each IP address in an event and tries to locate the zone associated with the IP address among the ordered list of networks. If a matching zone is found then the search is over, if not it moves with the order specified in the next network during SmartConnector configuration.
Networks
- Networks are ArcSight resources that are used to differentiate between the zones when IP ranges overlap.
- Local and Global are two standard networks configured for ESM.
- Network designations will enable the SmartConnector to tag the events with the correct zone such that the manager can find the correct model for assert events.
Customers
- The customers tagging is a feature that is developed to support Managed Security Services Provider (MSSP) environments.
- A customer will be considered as an “owner” of an event instead of considering it as a source or target of an event.
- The customer variables can be either a fixed string or a velocity template variable.
Event life Cycle in ArcSight
There are seven event life cycle in ArcSight ESM
- Data collection and event processing
The data is gathered from various sources and then it is processed. - Network model lookup and priority evaluation
Here we apply the logical setup of a network with the naming and structures so as to understand the environment, location, and then is set for priority evaluation. - Correlation evaluation
In this phase, the correlations will be evaluated and then will move to monitor and investigate. - Monitoring and investigation
The scenarios have to be properly understood to know what it is in order to monitor and is then allowed for investigation from an analyst so as to move to the workflow. - Workflow
In this phase, the workflow process model is implemented. - Incident analysis and reporting
Here we have to report the data and provide the analysis for what is obtained or received. - Event archival
Finally, the events will be archived into an external storage environment. The data can be stored for an extended period of time. An event is passed from all these seven stages.
Conclusion
The ArcSight tutorial gives you a clear vision of the usage and understanding of components that implement the compliance policy rules for detecting the vulnerabilities and resolving the issues with data management on security products.
About Author
A technical lead content writer in HKR Trainings with an expertise in delivering content on the market demanding technologies like Networking, Storage & Virtualization,Cyber Security & SIEM Tools, Server Administration, Operating System & Administration, IAM Tools, Cloud Computing, etc. She does a great job in creating wonderful content for the users and always keeps updated with the latest trends in the market. To know more information connect her on Linkedin, Twitter, and Facebook.
Upcoming Arcsight Training Online classes
| Batch starts on 11th Mar 2026 |
|
||
| Batch starts on 15th Mar 2026 |
|
||
| Batch starts on 19th Mar 2026 |
|


