Sonicwall Tutorial
Last updated on Jan 22, 2024
- What is a firewall?
- Intrusion Detection Systems
- Configuring Sonicwall firewall
- Configuring NAT Policy
- Conclusion
What is a firewall?
Firewalls can be applications or software that work at the organization level. They shield Private networks from outside clients and different organizations. They are a group of projects and their fundamental goal is to screen the traffic flow from outside to inside and the other way around. Their position is by and large behind a router or before the switch contingent upon the organization topologies. Their traffic rules are designed by the organization strategy rules. For instance, you block all approaching traffic to port POP since you would prefer not to get mail to be made sure about from all conceivable mail assaults. They log all the organization endeavors for a last review for you. They additionally can function as packet filters; this implies that the firewall makes the choices to advance or not the bundle dependent on source and objective locations and ports. Some of the mentioned brands are SonicWALL, Cisco ASA Series, Fortinet, Checkpoint, pfSense, and Juniper.
Learn new & advanced Architectures in SonicWall with hkr's Sonicwall Training
Why do we need a firewall?
Web connection makes us familiar to hackers who access our financial and individual data. The firewall functions as a hindrance, between our PC organization and the web. At the point when we are associated with the Internet and are continually deploying and getting data and can be handily hacked. SonicWALL is our first line of guard against security dangers and commands information over the Internet. Firewall is a boundary between Local Area Network (LAN) and the Internet. It permits maintaining private assets and limits the security hazards. It commands network traffic, in both directions. The given chart portrays a sample firewall between LAN and the web. The association between the two is the purpose of weakness. Hardware and the software can be utilized now to channel network traffic.
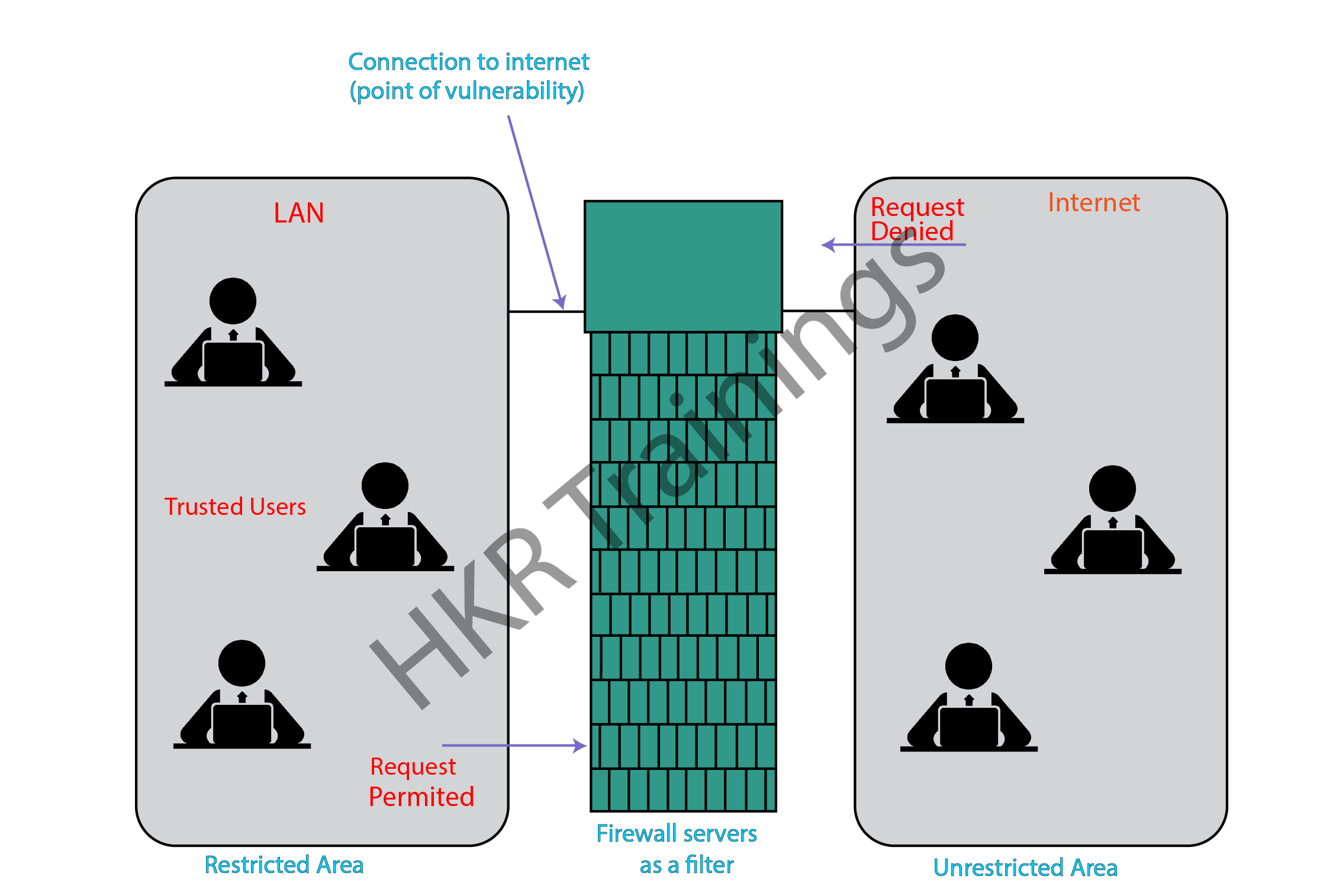
There are two sorts of Firewall framework: one operates by utilizing channels at the organization layer and other one functions by utilizing proxy servers at the client, application, or organization layer. Firewall management tended to be addressed through both framework administrators and the organization supervisors. The measure of filtering a firewall shifts. The measure of filtering might be diverse in various ways for a similar firewall.

Sonicwall Certification Training
- Master Your Craft
- Lifetime LMS & Faculty Access
- 24/7 online expert support
- Real-world & Project Based Learning
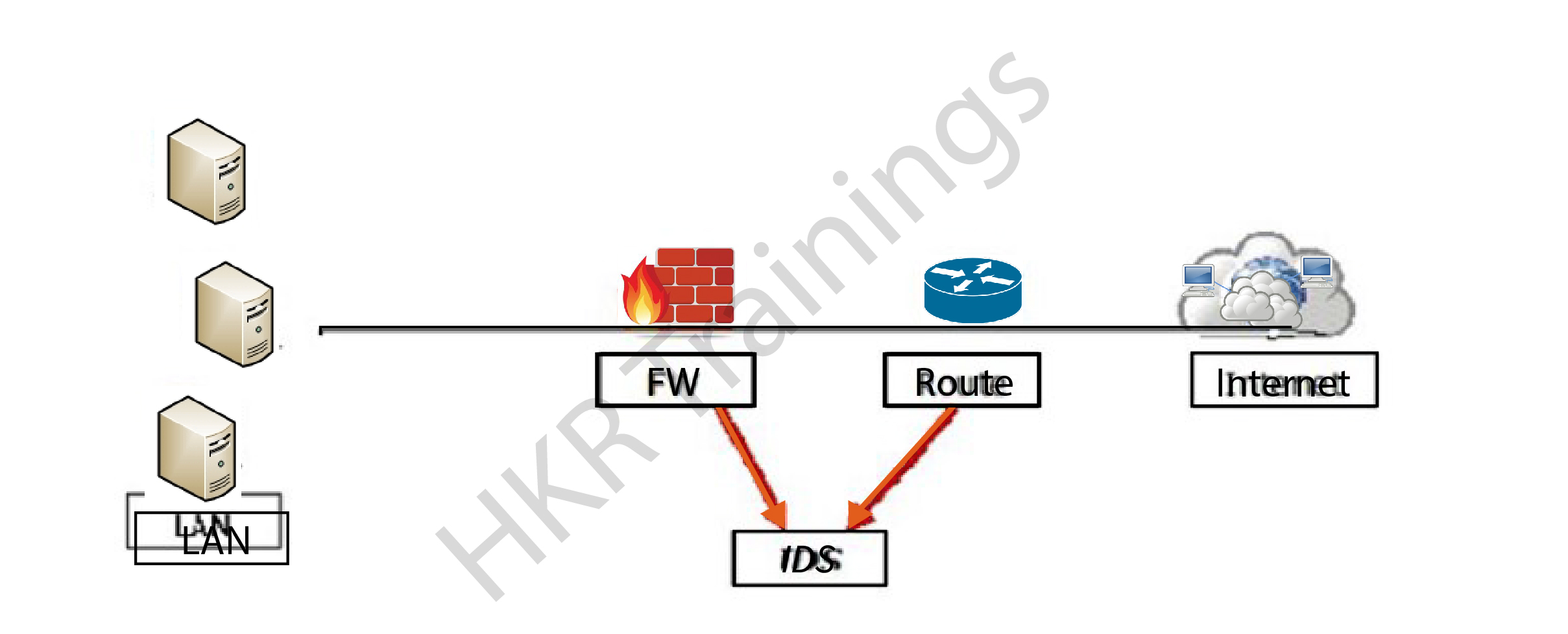
Intrusion Detection Systems
Interruption Detection Systems are just about as significant as the firewall since they assist us with recognizing the sort of assault which is being done to our framework and afterward to make an answer to block them. The monitoring part is like searching for suspicious signatures, tracing logs, and maintaining history of the occasions triggered. They assist the organization administrators to analyze the association integrity and genuineness which happen.
What is SonicWALL TZ 100?
The SonicWALL TZ 100 is an effective business strategy. It is a switch that brags of far and wide encryption capacities, VPN, and security similarity that gives discretionary Unified Threat Management (UTM) subscription administrations. It is good for distant and branch workplaces which should be safely associated with the principal headquarters’ workplaces. The organization security machine is an extraordinary firewall choice for independent venture associations that need network security, distant connectivity functionality, and minimal cost arrangement. A few VPN encryption and approval technologies are upheld, including 3DES, DES, AES, SHA-1, and MD5. Key exchange innovations that are upheld incorporate manual key, IKE, and L2TP over IPSec. Worldwide VPN customer platforms that are upheld incorporate Vista, Windows 2000, XP, and Windows 7, while the SSL VPN are upheld to incorporate Mac OS X and various Linux disseminations. TZ 100 arrangement gadgets are outfitted with SonicWALL's Global Management System (GMS). This exceptional component encourages unified administration of various SonicWALL gadgets, consequently bringing down arrangement and support costs for bigger associations because of its GMS. Capability and distantly oversees setups, consolidate strategies and announcing including management of real time execution.
Configuring Sonicwall firewall
Everybody from little non profit associations to medium-size and class organizations rely on SonicWALL gadgets to make sure about their organization correspondences. SonicWALL's exclusive SonicOS operating framework controls its firewall gadgets. Practically every SonicWALL gadget is presently fueled by the SonicOS Enhanced operating framework. The principal contrast between the two of them is the Enhanced adaptation empowers the framework's firmware to give zone management, ISP failover administrations, and WAN load adjusting.
The setup wizard: SonicWALL incorporates various wizards with its firewall gadgets. Accessible menus contrast by model. The Setup Wizard is an efficient apparatus which improves new router organization. If an organization is being updated, a SonicWALL gadget can be rearranged to manufacturing plant defaults and the Setup Wizard can be utilized to turn the gadget out once more.
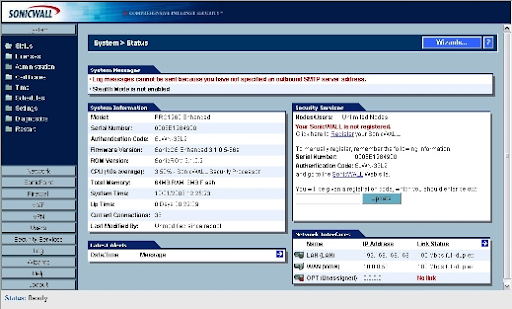
To utilize the Setup Wizard, sign in to a SonicWALL firewall and choose the Wizards button. The Wizards (Figure A) can be seen on the principle System Status page. The interaction utilizing a SonicWALL PRO 1260 is given here. Click the Wizards button, the SonicWALL Configuration Wizard shows four alternatives (Figure B)
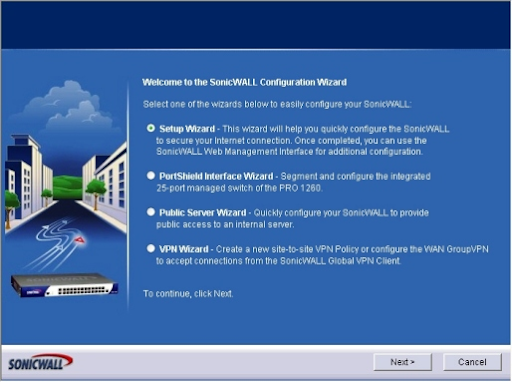
Indicate whether you want to choose the PortShield Interface Wizard, Setup Wizard, public
Server Wizard or VPN Wizard. For this model, we'll pick Setup Wizard and snap Next. The Setup Wizard shows up.
1. The Change Password screen shows up. Enter the default or old password key and another new password and affirm the new one. At the point when completed, click Next.
2. The Change TimeZone menu shows up. Check the box if you need the firewall to naturally adapt to sunlight saving time, and determine the relevant time region, and click Next.
3. The WAN Network Mode screen shows up. Choose the radio button demonstrating the strategy utilized to associate with your ISP.
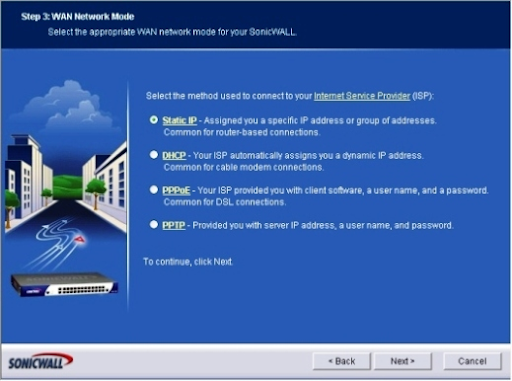
Click here to get latest Sonicwall interview questions & answers

Subscribe to our YouTube channel to get new updates..!
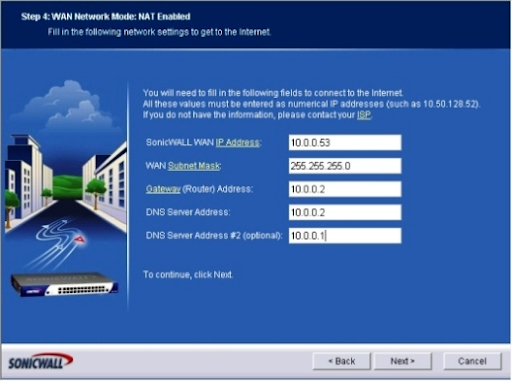
The WAN Network Mode: NAT Enabled menu shows up. Enter the WAN Subnet Mask, SonicWALL WAN IP Address, DNS Server Address, Gateway (Router) Address, and a secondary DNS address, and click Next. (Figure D)
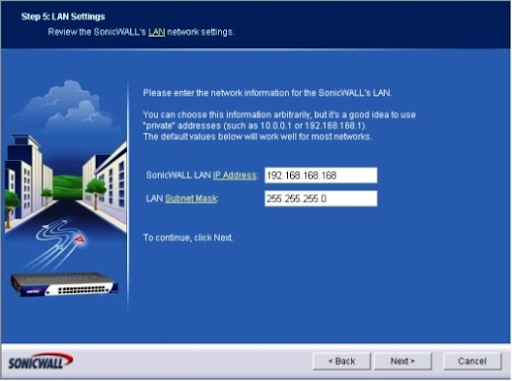
The LAN Settings menu shows up. Supply an IP address for SonicWALL's LAN. Make certain to give a subnet cover, and afterward click Next. (Figure E)
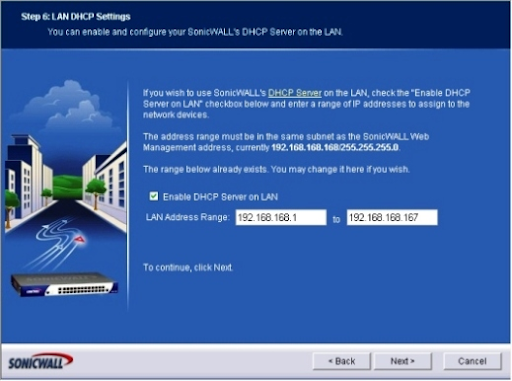
6. The LAN DHCP Settings screen shows up. Analyse the Enable DHCP Server On LAN box in the event that you need the SonicWALL gadget to give DHCP administrations. If you check the box, you'll need to enter the legitimate LAN address range. At the point when done, click Next. (Figure F)
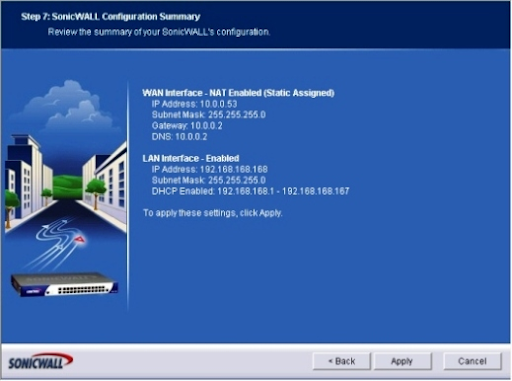
The SonicWALL Configuration Summary (Figure G). Survey the data wizard, and if all settings are right, click Apply. In the event that the arrangement requires change, click the Back button. A screen will show up demonstrating that the SonicWALL arrangement is being saved, and you'll be asked to pause. When the arrangement is finished, you'll see a Congratulations message expressing the progressions have been made and the Setup Wizard has finished.
NAT Policy
The Network Address Translation (NAT) engine in SonicWALL permits clients to characterize granular NAT policies for their approaching and active traffic. SonicWALL security gadget has a preconfigured NAT strategy to permit all PCs associated with the LAN to execute many to one NAT. It permits utilizing the IP address of the WAN interface, and an arrangement not to execute NAT when traffic across different interfaces. A NAT strategy gives us the adaptability to control Network Address Translation dependent on blends of Source IP address, Destination IP address, and Destination Services. Policy based NAT permits us to actuate various sorts of NAT simultaneously. Following NAT configurations are accessible in SonicWALL.
1. Many to One NAT Policy
2. Many to Many NAT Policy
3. One to One NAT Policy for Outbound Traffic
4. One to One NAT Policy for Inbound Traffic (Reflexive)
5. One to Many NAT Load Balancing
6. Inbound Port Address Translation via One to One NAT Policy
7. Inbound Port Address Translation via WAN IP Address.
Configuring NAT Policy
To configure a Many-to-One NAT policy which permits all PCs on the X1 interface to initiate traffic utilizing the SonicWALL security device’s WAN IP address, we require to execute the given steps:
- Navigate to Network > NAT Policies page and click on Add. Then the Add NAT Policy dialog box is shown.
- For Original Source, choose the option Any.
- For Translated Source, choose WAN Interface IP.
- For Original Destination, choose Any.
- For the Translated Destinations, choose Original.
- For Original Service, choose Any.
- For Translated Service, choose Original.
- For Inbound Interface, choose X1.
- For Outbound Interface, choose X1.
- Enter a short description in comment.
- Click on the Enable NAT Policy checkbox.
- Leave create a reflexive policy unchecked.
- Click Add.
Disadvantages of SonicWALL
SonicWALL router arrangement and sending is intricate and requires an exceptionally prepared expert for its establishment. Its innovation gives inconceivable and complex usefulness to its firewall capacities. For associations that require help, Remote Startup and Configuration Service for the TZ Series is accessible from a different scope of sellers.
Conclusion
SonicWALL firewalls are a strong hold of the small and medium business market. Utilizing the sonicwall firewall according to proper methods you can save your website from dangers and cyber threat. The steps to configure Sonicwall firewall is also provided in detail.
Related Articles
About Author
A technical lead content writer in HKR Trainings with an expertise in delivering content on the market demanding technologies like Networking, Storage & Virtualization,Cyber Security & SIEM Tools, Server Administration, Operating System & Administration, IAM Tools, Cloud Computing, etc. She does a great job in creating wonderful content for the users and always keeps updated with the latest trends in the market. To know more information connect her on Linkedin, Twitter, and Facebook.
Upcoming Sonicwall Certification Training Online classes
| Batch starts on 5th Mar 2026 |
|
||
| Batch starts on 9th Mar 2026 |
|
||
| Batch starts on 13th Mar 2026 |
|


