What is Ansible?
Ansible is an open-source configuration, system integration, and software delivery automation and orchestration tool. It aims to provide cloud infrastructure management and integration for both Unix-like and Windows devices. One of the standout features of Ansible is its ease of installation and client connectivity, making it a popular choice among users. Unlike other automation tools, Ansible does not require any special agents to be installed on client machines.
When it comes to executing tasks, Ansible leverages the power of SSH to establish connections with client systems. This eliminates the need for any additional software or agents on the client side. Ansible utilizes a push-based architecture, where modules containing specific tasks are sent to the clients. These modules are then executed internally on the client machines, and the output is seamlessly displayed back to the Ansible server.
While providing a simplified and agentless approach to automation, Ansible also offers a wide range of capabilities. It excels in automating cloud provisioning, continuous deployments, and zero-downtime rolling upgrades. Ansible's versatility extends to IT orchestration, allowing for the seamless coordination of tasks across multiple servers. This is made possible through the use of Python as the language of communication, enabling effective task distribution and execution.
In summary, Ansible is a powerful automation and orchestration tool that simplifies configuration management, system integration, and software delivery. Its agentless nature, ease of use, and extensive range of skills make it a popular choice for cloud infrastructure management. By leveraging SSH and Python, Ansible efficiently executes tasks on client machines and enables seamless chore orchestration, all without the need for servers as orchestrators.
Why Ansible?
Ansible is an open source confi
Here are some of the important benefits of using the ansible. They are:
- Everyone can use Ansible for free.
- Ansible is very consistent and lightweight, with no restrictions imposed by the operating system or underlying hardware.
- Because of its agentless capabilities and open SSH security features, it is extremely secure.
- Ansible requires special system administrator skills to install or use.
- Ansible has a seamless learning curve due to its extensive documentation and simple structure and configuration.
- Ansible's modularity in terms of plugins,inventories, modules, and playbooks makes it an ideal companion for orchestrating large environments.
Become a Ansible Certified professional by learning this HKR Ansible Training !
History of Ansible:
Here are some of the important points related to the history of ansible are:
- Ansible was created by Michael DeHaan, and the Ansible project began in February 2012.
- Cobbler and Func's creator is also the Fedora Unified network's controller.
- In 2015, RedHat purchased the Ansible tool.
- Ansible is included with the Fedora Linux distribution.
- Ansible is also obtainable for RedHat Enterprise Linux, Debian, CentOS, Oracle Linux, and Scientific Linux through Extra Packages for Enterprise Linux (EPEL) and Ubuntu, among other operating systems.
Workflow of Ansible:
Ansible works by connecting to your nodes and sending them small programs known as modules. In Ansible, modules are used to complete automation tasks.These programs are designed to be resource models of the system's desired state. Ansible then runs these modules and removes them when they are finished.To complete tasks without modules, you would have to rely on ad hoc commands and scripting.
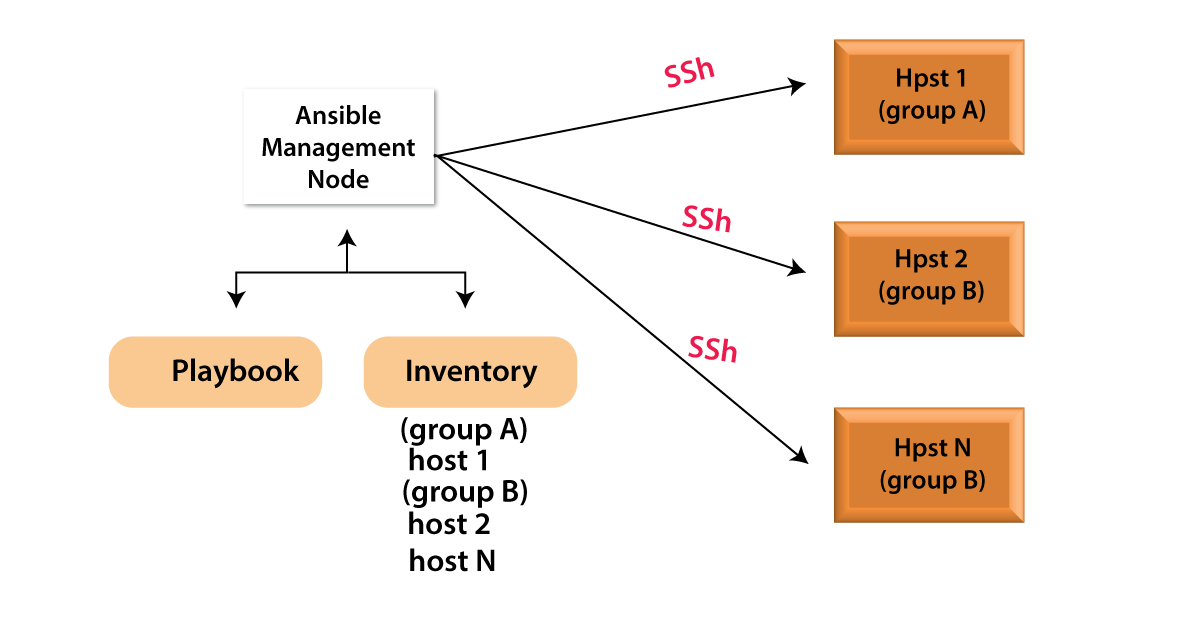
Ansible is agentless, that also means it does not involve any software to be installed on the nodes it manages.Ansible reads data from your inventory to determine which machines you want to manage. Although Ansible comes with a default inventory file, you can create your own and specify which servers you want Ansible to manage.
Ansible connects to servers and runs tasks using the SSH protocol.Ansible attaches to remote machines using your current user name and SSH keys by default. Root access is not required.Ansible connects to the remote machine(s) and transfers the modules required by your command or playbook for execution.
Ansible employs human-readable YAML templates, allowing users to automate repetitive tasks without having to learn a complex programming language.You can use Ansible's built-in modules to automate tasks, or you can write your own. Ansible components can be written in any language that supports JSON output, such as Ruby,Python, or bash. Powershell is even used to write Windows automation modules.
Ansible Architecture
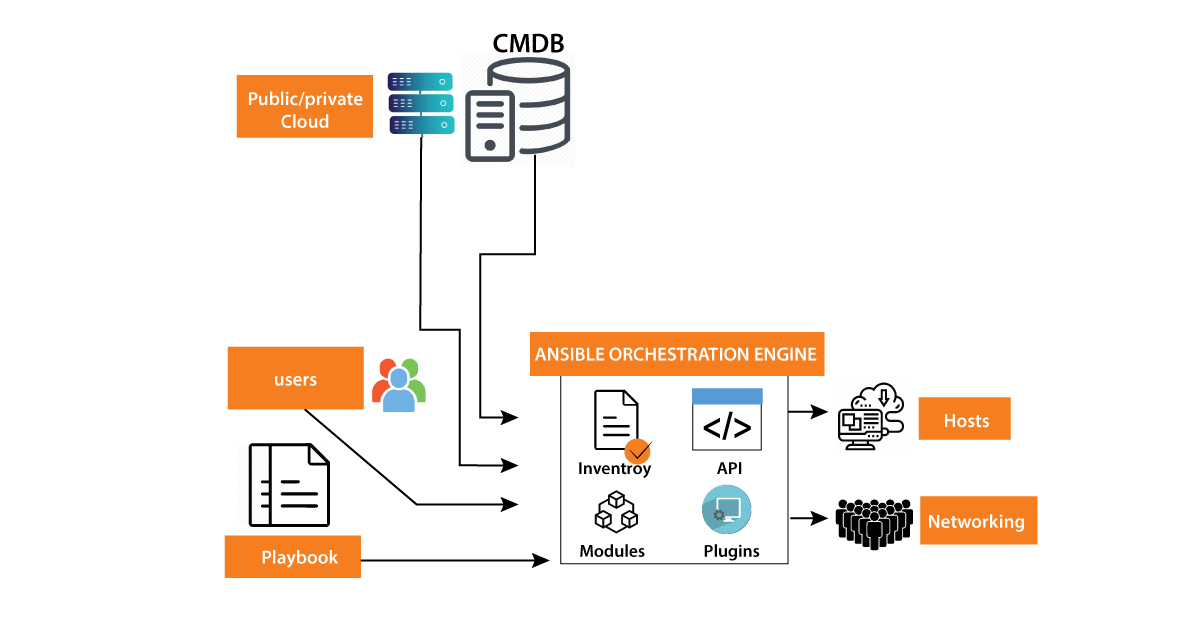
The architecture of Ansible encompasses several key components and functionalities. Let's delve into each of them in detail.
Firstly, the Ansible orchestration engine acts as the communication bridge between the user and the execution of Ansible playbooks. It facilitates interaction with both private and public cloud services, as well as a configuration management database, allowing for seamless orchestration of tasks.
An essential element of the Ansible architecture is the Inventory, which serves as a comprehensive list of nodes or hosts. This inventory includes vital information such as IP addresses, databases, servers, and other entities that need to be managed.
To enable integration with public or private cloud services, Ansible provides robust Application Programming Interfaces (APIs). These APIs act as conduits, facilitating smooth communication between Ansible and various cloud services, further enhancing its capabilities.
Ansible modules play a vital role in the architecture, as they establish connections with the nodes and distribute the Ansible module programs. These modules are executed by Ansible and subsequently removed. An intriguing aspect of these modules is their ability to run on any machine, eliminating the need for specific databases or servers. Additionally, changes in content can be tracked using a preferred text editor, terminal, or version control system.
Plugins are an important addition to the Ansible architecture, as they extend the core functionality of Ansible. There is a wide variety of pre-existing plugins available, and users also have the flexibility to create their own, offering a high level of customization.
Playbooks form a crucial component of Ansible's architecture. They consist of written code in YAML format, which describes the tasks and instructs Ansible to execute them. Playbooks can be used to launch tasks synchronously or asynchronously, providing flexibility and control over automation processes.
In the Ansible architecture, hosts refer to the node systems that Ansible automates. These hosts can include a range of machines, such as RedHat, Linux, Windows, and more, demonstrating the versatility of Ansible across different environments.
Ansible's architecture empowers users to automate networks efficiently. Its agentless automation framework, characterized by simplicity, security, and power, caters to both IT operations and development needs. Notably, Ansible employs a distinct data model that sets it apart from other automation engines, enhancing its effectiveness.
In addition, Ansible seamlessly integrates with cloud environments, allowing for the automation of tasks in remote server networks. By launching resources and instances on the cloud and connecting them to servers, Ansible facilitates remote task operations, providing users with enhanced operational capabilities.
Lastly, the architecture utilizes a Configuration Management Database (CMDB), which serves as a repository for storing and managing data. This data warehouse acts as a central hub, enabling efficient data management and organization within the Ansible ecosystem.
In conclusion, the architecture of Ansible encompasses various components such as the Ansible orchestration engine, Inventory, APIs, modules, plugins, playbooks, hosts, cloud integration, and CMDB. Together, these elements create a robust and versatile framework for automating tasks and managing IT operations, providing users with a comprehensive and efficient solution.
Related Article:Terraform vs Ansible
Installation of Ansible in Linux environment
When you've compared and weighed your options, and you've decided on Ansible. Then you should install it on your system. Let's walk through the installation process in various Linux distributions, such as:
Basic requirements:
- PyYAML is a YAML parser and emitter written in Python.
- Httplib2 is a large HTTP client library.
- Paramiko is a Python-native SSHv2 protocol library.
- RHEL/ CentOS/ Debian/ Ubuntu Linux are the available distributions.
- Jinja2 is a modern and user-friendly Python templating language.
- sshpass is a non-interactive ssh password authentication utility.
Here we are going to explain the installation step by step.
Installation on Redhat centos systems:
Step1: Install the EPEL repo
[root@ansible-server ~]# sudo yum install epel-release
Step2: Install the ansible package
[root@ansible-server ~]# sudo yum install -y ansible
Installation on Ubuntu systems:
Step1:First, perform a package update.
$ sudo apt update
Step2: Install the software properties common package
$ sudo apt install software-properties-common
Step3:Install the ansible personal package archive
$ sudo apt-add-repository ppa:ansible/ansible
Step4: Install the ansible
$ sudo apt update
$ sudo apt install ansible
Install the Ansible using pip:
The pip command is a Python package installation and management tool.
Step1: It wiek son the Linux and Unix systems
$ sudo pip install ansible
Installing the latest version of ansible:
Using portage:
$ emerge -av app-admin/ansible
In order to install the latest version, you need to uninstall the ansible package before emerging.
$ echo 'app-admin/ansible' >> /etc/portage/package.accept_keywords
Using pkg:
Ansible supports both Python 2 and Python 3, and FreeBSD has different packages for each python version. To install, follow these steps:
$ sudo pkg install py27-ansible
You can install from ports as well.
$ sudo make -C /usr/ports/sysutils/ansible install
Using OpenCSW:
Ansible is available as a SysV package from openCSW for Solaris:
- # pkgadd -d http://get.opencsw.org/now
- # /opt/csw/bin/pkgutil -i ansible
Using pacman:
Ansible is available in the community repository.
- $ pacman -S ansible
Installing using yum:
On fedora:
- $ sudo dnf install python-argcomplete
On RHEL and centos:
- $ sudo yum install epel-release
- $ sudo yum install python-argcomplete
By using apt:
- $ sudo apt install python-argcomplete
By using pip
- $ pip install argcomplete
[ Related Article : ansible training ]

Ansible Training
- Master Your Craft
- Lifetime LMS & Faculty Access
- 24/7 online expert support
- Real-world & Project Based Learning
Ad-hoc commands:
Ad-hoc commands serve as the easiest way to use the Ansible. They are advantageous when using commands on the multiple servers. By using these ad-hoc commands you can interact very easily with the servers. All the ad-hoc commands use the /usr/bin/ansible command line tool in order to automate a single task on multiple or single nodes. They are very quick and easy and are not preferred for re-use. These commands help in explaining the perfectness of the Ansible.
Syntax: ansible[-m ] -a -u [--become]
- Hosts:In the inventory for indicating the hosts we use all or “*”.
- Module_name:It serves as an optional parameter, by default it is a command and also there are several modules such as yum, apt, file, shell, etc.
- Arguments:In this section we are going to pass the values that are required by the specific module.
- Username:It is the command execution environment
- Become:It is an optional parameter and we use it when there is need to perform operations that require sudo privilege and by default it is set to false.
Top 30 frequently asked Ansible Interview Questions !
The different types of Ad-hoc commands are
- Parallelism and shell commands
By setting up the SSH agent you can reboot your company server in 12 parallel times at the same time.
$ ssh-agent bash
$ ssh-add ~/.ssh/id_rsa
To perform a reboot for all your company servers in 12 times as group you need to use the following option.
$ ansible abc -a "/sbin/reboot" -f 12
By default all the commands run from the current username account,if you want to change to another username the following option is required.
$ ansible abc -a "/sbin/reboot" -f 12 -u username
- File Transfer
By using the ad-hoc commands you can securely transfer files from one machine to another.For transferring files from one machine to server we use the following option.
$ ansible abc -m copy -a "src = /etc/yum.conf dest = /tmp/yum.conf"
In order to create a new directory we use:
$ ansible abc -m file -a "dest = /path/user1/new mode = 888 owner = user1 group = user1 state = directory"
And for deleting all the directories and files we use the following option as follows:
$ ansible abc -m file -a "dest = /path/user1/new state = absent"
- Managing packages
Ad-hoc commands are primarily used for yum and apt modules. In order to check whether the yum package is installed or not the following options are required.
To Check whether the yum is installed we use:
$ ansible abc -m yum -a "name = demo-tomcat-1 state = present"
To check whether the yum package is not installed we use:
$ ansible abc -m yum -a "name = demo-tomcat-1 state = absent"
In order to check whether the latest version is installed or not we use:
$ ansible abc -m yum -a "name = demo-tomcat-1 state = latest"
Managing users and groups
In order to create, remove or manage the user account on the managed nodes we use the following commands:
$ ansible all -m user -a "name=foo password=
$ ansible all -m user -a "name=foo state=absent"
- Gathering facts:
In order to known the discovered variable about the system we use:
$ ansible all -m setup
- Managing services
Ensuring whether the service is started on the webs servers we use:
$ ansible webservers -m service -a "name=httpd state=started"
Restart a web service on all the web servers we use:
$ ansible webservers -m service -a "name=httpd state=restarted"
In order to stop the service we use:
$ ansible webservers -m service -a "name=httpd state=stopped"
Related Article:Ansible sheell vs command !
Ansible playbooks:
Are there any compatibility considerations for Ansible Playbooks?
Ansible Playbooks are highly portable and compatible with Linux systems. This means that playbooks can be used across different Linux distributions and environments without compatibility issues. The portability of playbooks makes them a versatile automation solution, ensuring consistent execution across various Linux-compatible systems.
How do Ansible Playbooks execute tasks?
Ansible Playbooks utilize the Ansible Automation Engine to execute tasks. These tasks can be carried out either on a control system or a managed remote machine. The playbooks contain a set of human-readable instructions, written in YAML format, which are executed by the Ansible Automation Engine to automate the desired operations.
What tasks can be automated using Ansible Playbooks?
Ansible Playbooks enable IT teams to effectively automate various tasks, including those related to cloud infrastructure, virtualization, and other IT tools. Playbooks provide a flexible framework for automating a wide range of operations, making it easier to manage and orchestrate complex IT environments.
How are Ansible Playbooks written?
Ansible Playbooks are written using human-readable YAML files. Python developers can write playbooks quickly and effortlessly, similar to writing Python scripts. Playbooks can list and execute tasks just like regular Python code does, providing a familiar and intuitive approach to automation.
What are the advantages of Ansible Playbooks?
Ansible Playbooks offer several advantages. They are easy to write, allowing Python developers to quickly and effortlessly create playbooks similar to writing Python scripts. Additionally, the YAML format used in playbooks makes them human-friendly and easy to read, even for individuals without programming experience. Playbooks are also easy to debug, as any changes made while debugging do not affect execution, making issue identification simpler. Furthermore, Ansible Playbooks are highly portable and compatible with Linux systems.
Playbook structure:
Each playbook is made up of one or more plays. Plays are used to structure playbooks. A playbook may contain more than one play.
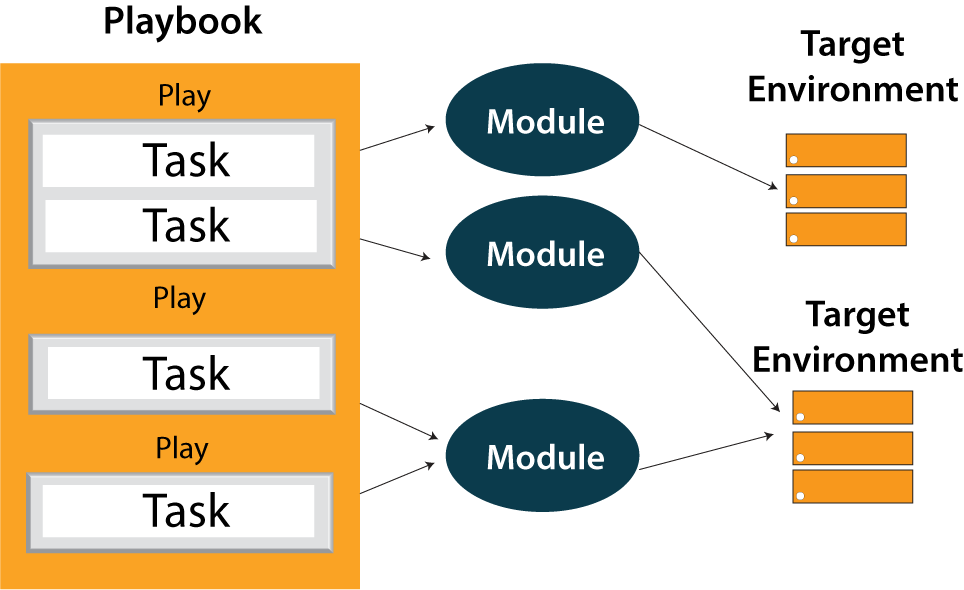
The play's function is to track a structured set of instructions against some specific host. There are various YAML authors available,but I chose to use a straightforward editor such as notepad++. To begin, open notepad++ and copy-paste the following YAML, then change the language to YAML. A YAML starts with 3 hyphens --- always.
In order to create the playbook the following basic syntax and save it as test.yml
---
name: install and configure DB
hosts: testServer
become: yes
vars:
oracle_db_port_value : 1521
tasks:
-name: Install the Oracle DB
yum:
-name: Ensure the installed service is enabled and running
service:
name:
Ansible roles:
Roles provide a structure for completely self-contained or interdependent collections of files, tasks, templates, variables, and modules.The primary mechanism for dividing a playbook into multiple files is the role. This simplifies the creation of complex playbooks and makes them more reusable. The playbook can be broken down into reusable components thanks to the playbook breaking.
Each role is restricted to a single functionality or desired output, with all of the steps required to achieve that result occurring either within the same role or in other roles listed as dependencies.Playbooks do not exist for roles. Roles are small pieces of functionality that can be used independently within the playbooks. Roles do not have a specific setting that determines which hosts the role will apply to.
Top-level playbooks serve as a link between the hosts in your inventory file and the roles that should be assigned to those hosts.
Creating a role:
Role structure is required to create the new role such as:role structure, usage and options.
Role structure: The riles had a saturated layout on the system and the default role structure is:
$ ansible-galaxy -h

Subscribe to our YouTube channel to get new updates..!
Usage:
ansible-galaxy [delete|import|info|init|install|list|login|remove|search|setup] [--help] [options] ...
Options:
- -h it shows help mode.
- -v verbose mode.
- --v it shows program version number and exit status.
Ansible variables:
The variable in a playbook is very similar to the variable in a programming language. It allows you to give a variable a value and use it anywhere in the playbook. You can use the variables in the playbook by putting conditions around their values.
Creation of valid variable names:
You need to create the valid variable names for using the variables.And variables should be letters, numbers and underscores. Foo_port is a valid variable name and Foo-port is an invalid variable name.
YAMl supports the libraries that map keys to values such as:
Foo:
Field1:one
Field2:two
Then you can reference to a specific field as follows:
foo[‘Field’]
Foo.field1
Ansible tags:
When you have a large playbook, it is useful to be able to run only a portion of it rather than the entire playbook. For this reason, Ansible includes a tag attribute.When you implement tags to items, you can control whether or not they are executed by including command-line options.
When you run a playbook, you can exhaust tasks based on tags in two ways, for example:
- Using the -tags or -skip-tags options on the command line.
- With the TAGS RUN and TAGS SKIP options in Ansible configuration settings.
Ansible command cheat sheet:
The commands used in ansible are:
- To install EPEL repo on Centos/RHEL systems.
[root@ansible-server ~]# sudo yum install epel-release
- To install Ansible packages on Centos/RHEL systems.
[root@ansible-server ~]# sudo yum install -y ansible
- To perform an update to the packages on Debian/Ubuntu systems.
$ sudo apt update
- To install the software properties-common-package on Debian/Ubuntu systems.
$ sudo apt install software-properties-common
- To install Ansible personal package archive on Debian/Ubuntu systems.
$ sudo apt-add-repository ppa:ansible/ansible
- To install Ansible on Debian/Ubuntu systems.
$ sudo apt update
$ sudo apt install ansible
- To issue a ping command on all servers defined in the inventory file named hosts.
[root@ansible-server test_ansible]# ansible -i hosts all -m ping
- To issue a ping command only on hosts2.
[root@ansible-server test_ansible]# ansible -i hosts all -m ping --limit host2
- To copy the file "testfile" on all hosts in the inventory file.
[root@ansible-server test_ansible]# ansible -i hosts all -m copy -a "src=/root/test_ansible/testfile dest=/tmp/testfile"
- To install the ncdu package on all hosts.
[root@ansible-server test_ansible]# ansible -i hosts all -m yum -a 'name=ncdu state=present'
- To remove the ncdu package on all hosts.
[root@ansible-server test_ansible]# ansible -i hosts all -m yum -a 'name=ncdu state=absent'
- To build the directory structure for the role named role1.
[root@ansible-server test2]# ansible-galaxy init role1
To dry-run p4.yml playbook.
[root@ansible-server test_ansible]# ansible-playbook -i hosts p4.yml --check
- To run a p4.yml playbook with password authentication for all hosts.
[root@ansible-server test_ansible]# ansible-playbook -i hosts p4.yml -k
Ansible modules
Ansible modules are discrete units of code that can be used from the command line or as part of a playbook task.In Ansible, modules are also known as task plugins or library plugins.Ansible comes with a set of modules known as the module library, which can be executed directly or remotely via the playbook.
Modules can also be written by users. These modules can control things like services, system resources, files, and packages, as well as handle system command execution.
Let's take a look at how to run three different modules from the command line.
- ansible webservers -m service -a "name=httpd state=started"
- ansible webservers -m ping
- ansible webservers -m command -a "/sbin/reboot -t now"
Taking arguments is supported by all modules. Generally, all modules accept key=value arguments that are separated by spaces.Some modules require no arguments, while shell/command modules require the command string to be executed.
Ansible modules execute in a manner very similar to that of a playbook, such as:
- name: reboot the servers
command: /sbin/reboot -t now
Another method for passing arguments to a module that uses YAML syntax is known as complex args.
- name: restart webserver
service:
name: httpd
state: restarted
Technically, all modules return JSON format data, but you don't need to know much about that if you're using command line or playbooks. If you're writing your module, it means you don't have to write modules in any language other than the one you choose.
Modules should be invertible, meaning they should not make changes if the current state matches the desired final state. When using Ansible playbooks, these modules can cause "change events" by informing "handlers" to perform additional tasks.The Ansible-doc tool can be used from the command line to access documentation for each module:
ansible-doc yum
Ansible Templates:
A template is a document that stores all of your configuration parameters, but the flexible values are specified in Ansible as variables. The variables will be supplemented with the influencing factors mostly during playbook execution, depending on the severity including which cluster you are using.
With the Jinja2 templating engine, you can do more than just replace variables. Loops, conditional statements, macros, filters for data transformation, arithmetic calculations, and so on are all possible.
Typically, template files can have the.j2 extension, which signifies the use of the Jinja2 templating engine.
The variables in a template file will be denoted by double curly braces, '{{variables}}'.
While using the Ansible Template module, we need two parameters, such as:
- src: The template file's source. It can take both a relative and an absolute path.
- dest: The remote server's destination path is denoted by dest.
The template module attributes are force, mode,backup and group.
Ansible YAML:
YAML is used to identify setup, which has grown in popularity in recent years thanks to the use of Ansible and SaltStack.In contrast to other regular data formats such as XML or JSON, YAML is easier for humans to read and write. Most programming languages include libraries for working with YAML.
Every YAML file in Ansible begins with a list. Each item in the list is a collection of key-value pairs, also known as a "hash" or "dictionary." As a result, we must understand how to write lists and dictionaries in YAML.YAML has another minor quirk. All YAML files can preferably begin and end with ---. This is part of the YAML format and represents the beginning and end of a document.
A list's members are all lines that begin at the same indentation level, beginning with a "-" (a dash and space):
Example:
---
# A list of flowers
- Rose
- Lilly
- Jasmine
- Lotus
---
Ansible Commands:
The Ansible command module is often used to execute any commands or scripts on a remote target machine. Alternatively, it can be used to execute commands on a remote node.The command module is used to execute simple Linux commands on a remote node or server that is a member of the host group or a standalone server that is mentioned in the host group.
The shell module should be used when we need to run a command in a remote server's shell of your choice. By default, the commands are executed through the /bin/sh shell. You can use various operations such as '|', ", '>', and so on, as well as environmental variables such as $HOME.
Ansible inventory:
The inventory is a list or group of lists that Ansible uses to work against multiple managed hosts in your infrastructure at the same time.Once an inventory has been defined, you can use patterns to select which hosts or groups to run Ansible against.
The inventory file's default location is /etc/ansible/hosts. You can also use the -i path> option to specify a different inventory file at the command line. The inventory file can be retrieved from dynamic or cloud sources, or in a variety of formats (YAML, ini). Ansible has inventory plugins that allow it to be flexible and customizable.
Ansible debug:
Ansible includes a debug module that makes tasks easier to manage. It is a useful tool for determining any problem areas.Ansible version 2.1 added a verbosity parameter to the debug module, converting it from a print line.
Example:
--
- name: Debug Example - Hello World
hosts: localhost
tasks:
- name: Print debug message
debug:
Ansible file:
The Ansible file module has been used to create and delete files or folders on a remote server. You can also create and delete directories, as well as change the data's permissions.You can also make and delete soft links (symlinks) and hard links. You can change the permissions of files using the Ansible file module.
For creating and deleting the file in the remote server we mainly use two parameters such as path and state. Path is nothing but the path of the file in the remote server and state parameter mention the touch.
Ansible Vault:
The Ansible Vault feature enables users to encrypt values and data structures within Ansible projects. This allows you to secure any secrets or sensitive data that is required to run Ansible plays but should not be publicly visible, such as private keys or passwords. When the key is provided, Ansible automatically decrypts the vault-encrypted content at runtime.
To incorporate these secrets with regular Ansible data, both the Ansible and Ansible-playbook commands, which are used to execute ad hoc tasks and structured playbooks, have support for decrypting vault-encrypted content at runtime. Ansible Vault is built with file-level granularity, which means that files are either completely encrypted or unencrypted. It employs the AES256 algorithm to provide symmetric encryption.
Comparing with other tools:
Ansible vs chef vs puppet
Definition:
- Ansible:Ansible is a free and open-source IT engine for automating application deployment, cloud provisioning, intra-service orchestration, and other IT tools.
- Chef:The chef is a robust automation platform that converts infrastructure into code. Whether you are running on-premises, in the cloud, or in a hybrid environment.
- Puppet:Puppet is a server configuration management tool that can be used to configure, deploy, and manage servers.
Setting up:
- Ansible is only running a master on the server machine, but no agents are running on the client machine. It logs in to client systems or the nodes you want to configure via an SSH connection. Client machine virtualization does not necessitate any special configuration. That is why it is quicker to set up!
- Chef's architecture is based on a master-agent model. Chef server is installed on the master machine, and Chef client is installed on each client machine as an agent. There is also an additional component known as workstation, which contains all of the tested configurations and is then pushed to the central chef server. That is why it is not so simple.
- Puppet has a master-agent architecture as well. Puppet server is installed on the master machine, and Puppet clients are installed on the client machine as an agent. Following that, a certificate signing occurs between the agent and the master. That is why it is difficult to set up.
Interoperability:
- The Ansible server must be installed on a Linux/Unix machine. Ansible also works on Windows machines.
- Puppet Master is only available for Linux/Unix, but Puppet Agent is also available for Windows.
- Chef Server is only available on Linux/Unix, but Chef Client and Workstation are also available on Windows.
Configuration Language:
- Ansible makes use of YAML (Python). It is simple to learn and geared toward administrators.Python is built into the majority of Unix and Linux deployments, making it easier to get the tool up and running.
- Chef employs the Ruby Domain Specific Language (Ruby DSL). It has a steep learning curve and is geared toward developers.
- Puppet employs a puppet Domain Specific Language (Puppet DSL). It is difficult to learn and is geared toward system administrators.
What are some alternative IT automation tools to Ansible?
When looking for alternative IT automation tools to Ansible, there are several options available.
One such tool is SaltStack, which provides automation solutions for system provisioning, configuration management, and software deployments. It is widely used by various organizations with diverse needs.
Another popular choice is Chef, an automation tool that specializes in DevOps lifecycle management. It offers streamlined automation for application setup, deployment, and administration, catering specifically to enterprise requirements.
Puppet is another noteworthy automation tool that simplifies application deployment, setup, and administration. Its powerful language for defining system states and their actions makes it a preferred choice for many.
For infrastructure automation, Terraform is a prominent tool that can handle tasks like planning, provisioning, and management of resources through code. It effectively automates complex operations, including network creation.
CloudFormation, offered by AWS, is an automation tool specifically designed for cloud infrastructure. It assists in designing and administrating cloud resources by facilitating the coding of infrastructure resources.
In the case of Azure, Resource Manager is an automation tool that automates the coding definition and deployment of Azure Resource Manager cloud resources. It provides a streamlined approach to managing resources on the Azure platform.
Lastly, Jenkins is another popular open-source automation tool that can be used with Ansible. It offers extensive automation capabilities across various stages of the software development process.
These are just a few examples of alternative IT automation tools to Ansible that cater to different levels of complexity and meet the diverse needs of organizations.
What are the differences between core modules and extra modules in Ansible?
In Ansible, there are two types of modules available: core modules and extra modules. Core modules are preinstalled and come with Ansible out of the box. These modules have been extensively tested and are designed to provide quick and efficient installation, configuration, and administration of various applications and services.
On the other hand, extra modules are additional modules that are not included by default in the core Ansible installation. These modules can be obtained from Ansible's Extras repository and are to be acquired and used at your discretion. Extra modules are typically used for managing cloud services and deploying software using specific components that may not be available in the core modules.
The key distinction between core modules and extra modules lies in their availability and purpose. Core modules are readily accessible and provide a foundational set of functionalities for common system administration tasks. Extra modules, however, offer more specialized capabilities and are meant to address specific needs, like managing cloud services or deploying software in specific environments.
Overall, both core modules and extra modules contribute to the flexibility and extensibility of Ansible, allowing users to tailor their automation setups based on their unique requirements.
What is Ansible Tower or Tower Ansible?
Ansible Tower, also known as Tower Ansible, is a powerful orchestration tool designed to manage virtual and cloud infrastructure, as well as applications. It offers automation capabilities for IT management, making it an essential component of orchestrator applications like the Orchestrated IT Infrastructure Management Tool for SUSE Linux Enterprise Server 11.
With Ansible Tower, IT professionals can easily monitor an entire server network directly from within the Ansible platform. It facilitates the distribution of multiple applications across remote nodes, ensuring efficient deployment. Additionally, Ansible Tower contributes to infrastructure security by providing advanced management capabilities for Ansible roles and playbooks.
One of the key features of Ansible Tower is its ability to serve as a data warehouse. It helps administrators maintain control over data expansion by centralizing storage and management. Data management within Ansible Tower is web-based, allowing integration and analysis of information from various sources. The platform supports secure data sharing based on defined security policies.
Ansible Tower excels in managing inventories, configuring nodes, and scheduling jobs efficiently. It enables administrators to easily handle nodes, playbooks, and inventories, not limited to just servers but also including network devices, databases, web servers, and virtual computers. Furthermore, Ansible Tower provides comprehensive management capabilities for applications and databases such as WordPress, Drupal, Joomla, MySQL, PostgreSQL, and MongoDB.
Overall, Ansible Tower or Tower Ansible is a robust tool that empowers IT professionals to automate and streamline the management of infrastructure and applications, enhancing efficiency and security throughout the entire system.
What are the benefits of using Ansible modules for multi-system node management?
What are the advantages of using ad-hoc commands in Ansible?
Ad-hoc commands offer several advantages in Ansible. They are quick and easy to use, enabling efficient interaction with servers. They are particularly useful for executing commands on multiple servers simultaneously. Ad-hoc commands are great for tasks that do not require extensive configuration or complex orchestration. However, they are not recommended for tasks that need to be reused or require more advanced automation capabilities provided by playbooks.
What is the purpose of using ad-hoc commands in Ansible?
Ad-hoc commands serve as the easiest way to use Ansible for executing commands on multiple servers. They allow for quick interaction with servers without the need for writing extensive playbooks. Ad-hoc commands utilize the "/usr/bin/ansible" command line tool to automate single tasks on multiple or single nodes. They are particularly useful for one-time tasks or situations where reusability is not a priority.
How do Ansible modules benefit multi-system node management?
Ansible modules greatly benefit multi-system node management by standardizing the process. They help decrease administrator workload and improve IT infrastructure management. By using modules, tasks can be automated and executed consistently across multiple systems, ensuring uniformity and reliability. The flexibility and ease-of-use provided by modules make it easier to manage and administer apps and services across different nodes, leading to efficient and streamlined operations.
What are the different types of modules offered by Ansible?
Ansible offers both core modules and extra modules. Core modules are preinstalled tested components that come with Ansible. They provide essential functionalities for installing, configuring, and administering apps and services. On the other hand, extra modules can be acquired as needed from Ansible's Extras repository. These additional modules expand the capabilities of Ansible and cater to specific requirements, such as cloud service management or software deployment services.
What are Ansible modules and how do they work?
Ansible modules are discrete activities designed to be executed individually or as part of a playbook. They serve as a way to quickly install, configure, and administer apps and services. Similar to IATA/ITAR packages used in transportation networks, they provide a means to transmit messages within IT systems. Modules offer flexibility and ease-of-use, allowing for standardized multi-system node management.
What are Ansible modules and how are they used?
Should changes be made by Ansible modules if the current state already matches the desired final state?
Ansible modules should be designed to be invertible, meaning they should not make changes if the current state matches the desired final state. This ensures that modules do not unnecessarily modify the system and cause unintended consequences. By adhering to this principle, modules can maintain the desired state of the system without introducing unnecessary changes, ensuring efficient and reliable execution of tasks.
What do Ansible modules offer as an alternative?
Ansible modules offer an effective alternative for executing discrete activities individually or as part of a playbook. They provide flexibility while remaining easy to use. Instead of relying on IATA/ITAR packages, Ansible modules offer a more streamlined and efficient approach to transmitting messages and managing various tasks within a transportation network or IT infrastructure.
What is the role of multi-system node management in Ansible?
Multi-system node management plays a crucial role in Ansible. By standardizing this management using Ansible modules, administrators can reduce their workload and improve the overall management of IT infrastructure. Ansible modules provide flexibility and ease of use, allowing for efficient management of multiple systems.
What are core modules and extra modules in Ansible?
Ansible offers both core modules and extra modules. Core modules are preinstalled components that come with Ansible. They are tested and allow for quick installation, configuration, and administration of apps and services. On the other hand, extra modules are not preinstalled but can be acquired from Ansible's Extras repository as needed. They provide additional functionality, such as cloud service management and software deployment services.
What are IATA/ITAR packages and how are they related to Ansible modules?
IATA/ITAR packages are used to transmit messages within transportation networks. They are mentioned in relation to Ansible modules to draw a comparison in terms of their purpose and function. Ansible modules are similar to IATA/ITAR packages in the sense that they are discrete activities designed to be executed individually or as part of a playbook.
Conclusion
In the above ansible tutorial all the concepts are covered in depth. This tutorial will help learners and professionals as well in order to get deep insights of the ansible platform at a glance. Moreover if you find any information or topic not covered in the tutorial please drop a message in the comments section, we will definitely consider them.
About Author
As a senior technical content writer for HRK tainings, srivalli patchava has a greater understanding of today's data-driven environment, which includes key aspects of data management and IT organizations. She manages the task of creating great content in the areas of software testing, DevOps, Robotic process automation. Connects with her on Linkedin and Twitter.
Upcoming Ansible Training Online classes
| Batch starts on 13th Mar 2026 |
|
||
| Batch starts on 17th Mar 2026 |
|
||
| Batch starts on 21st Mar 2026 |
|

